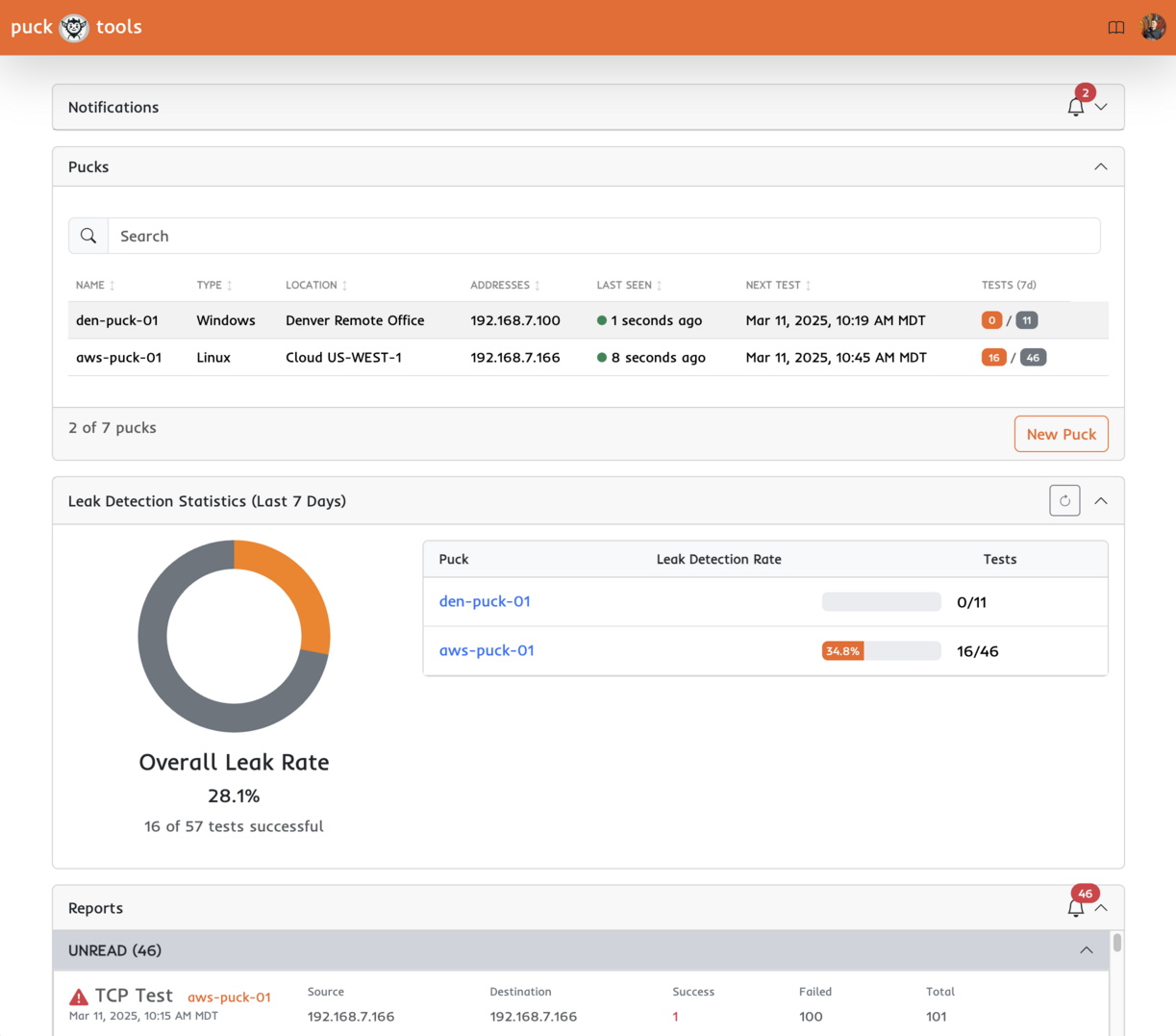
Find network leaks
Puck tests outbound network protections. Easily validate firewalls by dropping a puck in your network. Puck tests common egress paths using protocols and ports often abused by malicious actors for C2, malware and data exfiltration. If any leaks are found you get an alert, easy, one less thing to worry about.
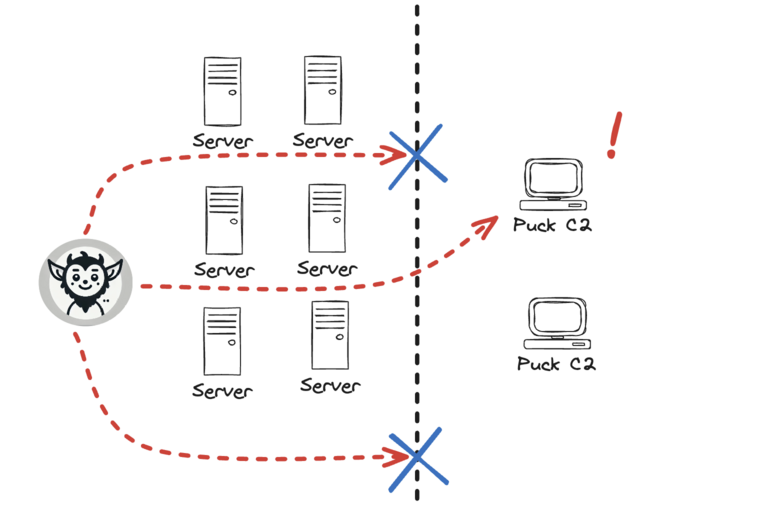
How it works
Deploy pucks inside your secure networks. The puck will attempt to connect out to our managed command and control (C2) servers and transfer fake data. You get notified if any of the attempts are successful. This simple workflow allows you to check your network for leaks and ensure your network detections are working as expected. Still have questions? Check out the docs
Pricing
Puck is a simple way to test outbound network protections. Drop a puck in your network and it begins testing egress paths using protocols often abused by malicious actors. If any leaks are found you get an alert, easy, one less thing to worry about.
Enterprise
$7500/yr
- 5 pucks (instant download)
- Unlimited notifications
- Test multiple protocols
- $500 per additional puck
Find leaks
Simple
Puck can be deployed anyway you need. As a physical device, as software you install on your computer or as a container you run in your cloud. No remote systems to manage and puck supports multiple protocols including HTTP, HTTPS, TCP, UDP and DNS.
Safe
Puck will only try to make network connections to test filters. No scanning, no sniffing. Puck doesn't have access to any of your sensitive data and can't run any commands.
Secure
Puck finds misconfigurations and network leaks quickly and alerts you. Rest knowing your networks are segmented and your detections are working as expected.
Frequently Asked Questions
Deploying a puck helps you:
- Validate firewall rules: Ensure your outbound network protections are working correctly
- Detect network leaks: Find misconfigurations that could allow unauthorized data exfiltration
- Test security controls: Verify that your network segmentation and monitoring systems are effective
- Compliance validation: Demonstrate that your security controls meet regulatory requirements
- Proactive security: Identify vulnerabilities before they can be exploited by malicious actors
Puck offers multiple deployment options to fit your environment:
- Software installation: Download and install puck software on existing Windows, Linux systems
- Docker container: Run puck as a container in your cloud or on-premises infrastructure
- Virtual machine: Deploy puck as a VM image for virtualized environments
- Physical device: Plug-and-play hardware puck that you can place anywhere in your network
All deployment methods are equally effective - choose the option that best fits your security policies and infrastructure.
Puck tests common egress paths and protocols that malicious actors and malware frequently abuse:
- Common C2 ports and protocols: Ports 80, 443, 53, 8080, 8443, and others
- HTTP/HTTPS: Web-based command and control channels
- DNS: DNS tunneling and data exfiltration techniques
- TCP/UDP: Direct socket connections on various ports
Puck only attempts outbound connections - it never scans your network or accesses sensitive data.
Yes, puck is designed to be completely safe for production use:
- Read-only operation: Puck cannot modify any files or system settings
- No data access: Puck doesn't have access to your sensitive data or credentials
- Outbound only: Puck only makes outbound connections, never accepts incoming connections
- Controlled testing: All network activity is limited to specific test protocols and ports
- No persistence: Puck doesn't install services or create persistent processes
Puck's behavior is predictable and limited to network connectivity testing only.
Puck provides multiple notification options:
- Web dashboard: Real-time alerts and detailed reports in your puck dashboard
- Email notifications: Immediate email alerts when leaks are detected
- Webhook integration: Send alerts to your existing security tools and SIEM systems
- Slack/Teams: Direct integration with popular collaboration platforms
- API access: Programmatic access to puck data for custom integrations
Configure your preferred notification methods in the puck dashboard to stay informed about any detected network leaks.
Puck is commonly used for:
- Breach and Attack Simulation (BAS): Regular testing of security controls
- Compliance validation: Meeting regulatory requirements for security testing
- Network segmentation verification: Ensuring proper isolation between network zones
- Firewall rule validation: Testing that outbound restrictions are working
- Security awareness training: Demonstrating the importance of network security
- Incident response preparation: Understanding your network's security posture
- Vendor security assessments: Testing third-party network security
Puck helps organizations of all sizes maintain confidence in their network security posture.